With Cloudflare, you can generate an origin certificate, it’s a free TLS certificate signed by Cloudflare and you can install it on your web server to secure connection between your server and the Cloudflare proxy servers. The main feature of Cloudflare origin certificates is the certificate validity, which can be set to up to 15 years, and the ability to include all your subdomains with a wildcard *.yourdomain.com.
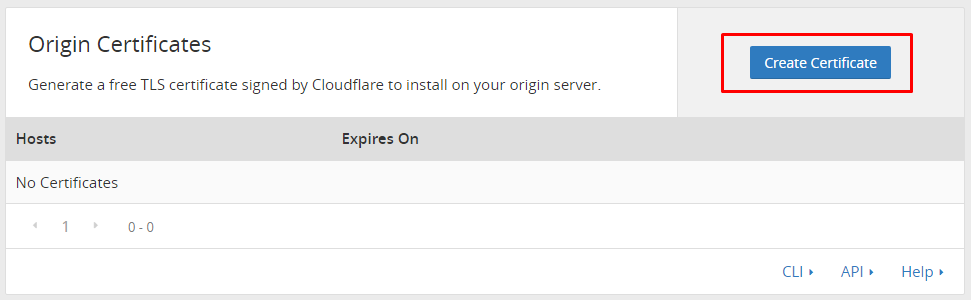
Create your origin certificate
At first, go into your Cloudflare dashboard and in the section Crypto, click on create a certificate.
If you have already generated a CSR (Certificate Signing Request) and a private key, you can copy your CSR content to generate your Cloudflare Origin certificate, otherwise you can let Cloudflare generate a private key for you and click on next to generate your certificate. We recommend you to choose an ECDSA private key rather than RSA, because ECDSA provide better performance and encryption level than RSA.
After you click on the button next, Cloudflare will display your private key and your origin certificate.
Make sure to save your private key before closing your web browser tab because Cloudflare will not display it anymore.
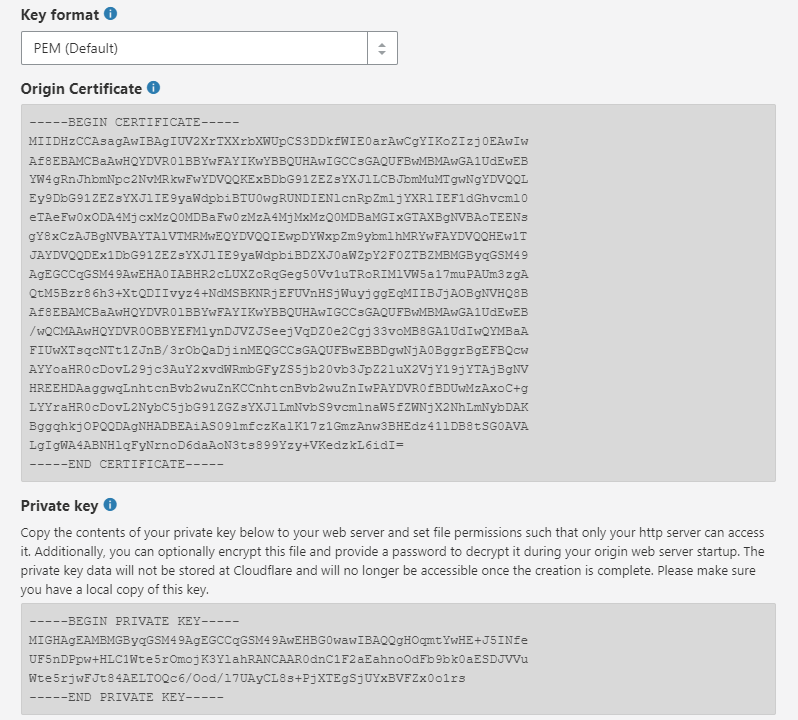
Create a new file yourdomain-tld-key.pem and copy the content of your private key inside this file, then create another file yourdomain-tld-cert.pem and copy the content of your origin certificate inside this file. To store your private key and your origin certificate, you can create a folder in /etc/nginx. In our example, we have put our certificate and our private key in /etc/nginx/ssl.
Add Cloudflare Root certificates authorities (optional)
This step is optional because Nginx will not attempt to validate the chain of your Origin CA certificate, it will only check if there is no error in your SSL certificate and in your private key.
To add Cloudflare Root certificates authorities to your Origin certificate, you have to download them from Cloudflare website and to merge your origin certificate with the root certificate.
You can download Cloudflare root certificate with the following command :
# For RSA private keys
wget -O cloudflare_root.pem https://support.cloudflare.com/hc/en-us/article_attachments/206709108/cloudflare_origin_rsa.pem
# For ECDSA private keys
wget -O cloudflare_root.pem https://support.cloudflare.com/hc/en-us/article_attachments/206709098/cloudflare_origin_ecc.pem
To merge your origin certificate and the Cloudflare Root certifcate, you can use the command cat :
cat yourdomain-tld-cert.pem cloudflare_root.pem > yourdomain-tld-cert.pem
Install your origin certificate with Nginx
Your origin certificate can now be installed with Nginx. To do so, you have to edit your Nginx vhost (or to create a file ssl.conf in /var/www/yourdomain.tld/conf/nginx if your server is running with EasyEngine) and to add SSL/TLS configuration by following this example :
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl on;
ssl_certificate /etc/nginx/ssl/yourdomain-tld-cert.pem;
ssl_certificate_key /etc/nginx/ssl/yourdomain-tld-key.pem;
If your server is running with Nginx 1.15.0 or a newer release, you can remove the line ssl on;
Reload your nginx configuration with nginx -t && service nginx reload
Your Cloudflare origin certificate is now installed on your server, so you can change the SSL settings to “Full (strict)” in your Cloudflare dashboard.
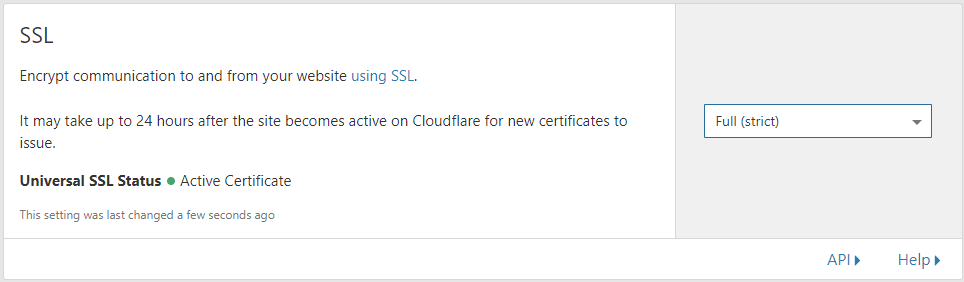
If you want to force redirection from http to https, you can enable the options “Always use HTTPS” and “Automatic HTTPS Rewrites” using your Cloudflare dashboard.
otherwise you can create a file force-ssl-yourdomain.conf into /etc/nginx/conf.d/ with the following content :
server {
listen 80;
listen [::]:80;
server_name yourdomain.com www.yourdomain.com;
return 301 https://yourdomain.com$request_uri;
}